The Calamu Process
Calamu’s patented process ensures that data is always available to authorized users and applications, and completely valueless to everyone else.
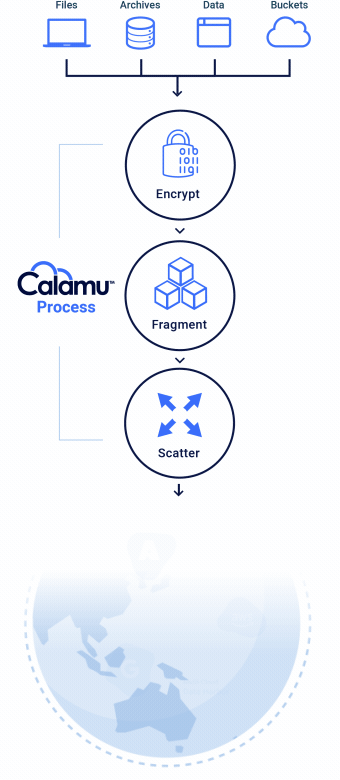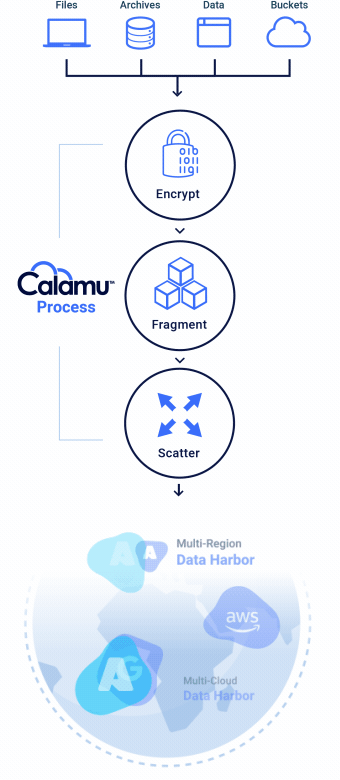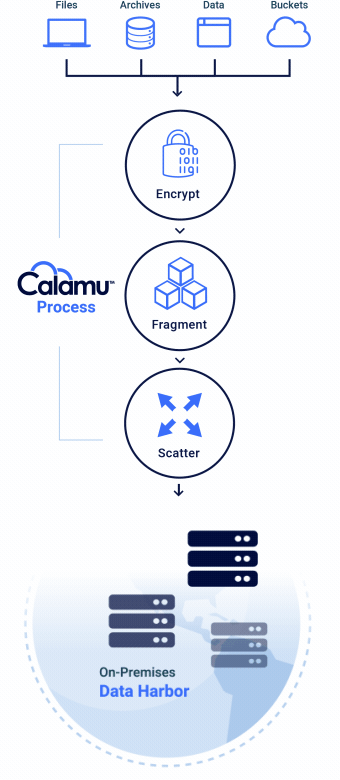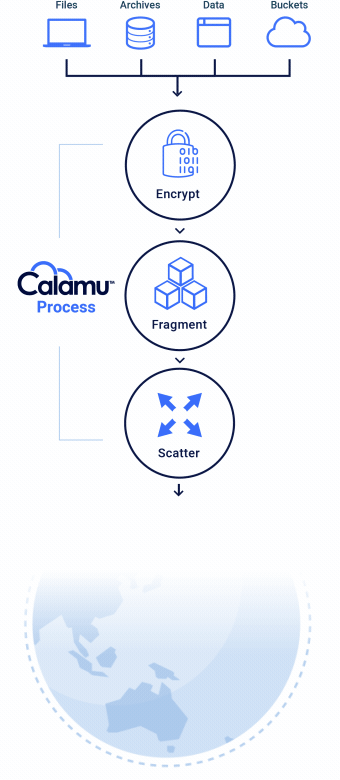
How it Works
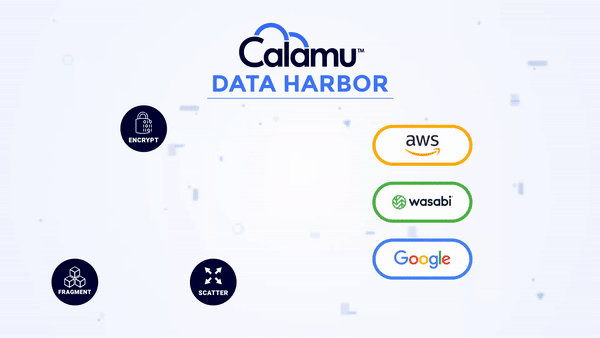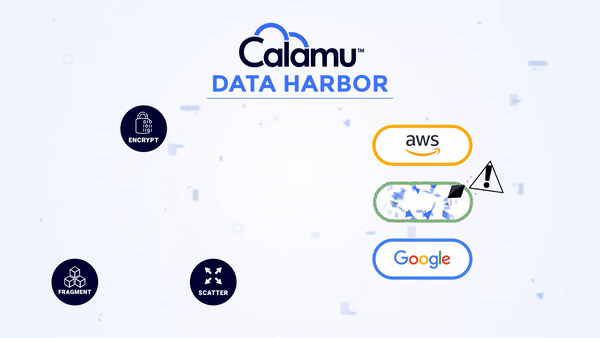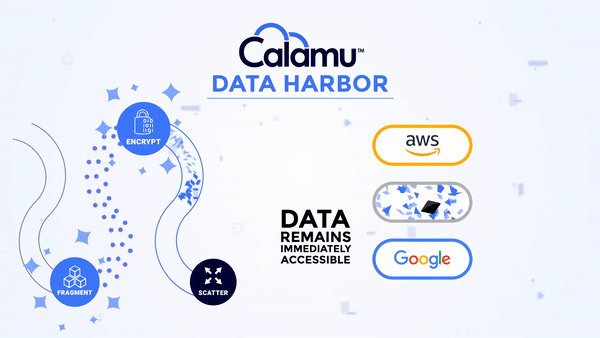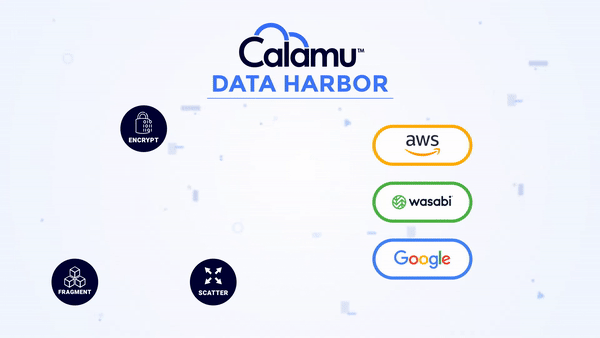
Calamu can be deployed in the cloud or on-premises and supports Kubernetes. The platform works by processing data from S3-API compatible applications, local file servers, and end-user devices, protecting data while at-rest and in-motion. Data is automatically fragmented and scattered across multiple separate storage locations, creating a virtual environment known as a Data Harbor. Seamlessly and transparently, the data can then be automatically reassembled, or “reconstituted” at the source in real-time by authorized users and applications.
Watch the Video
The Calamu process enables zero-trust, end-to-end security that is unparalleled by legacy solutions.
Eliminates Data Sensitivity
With a Data Harbor, your data is completely in your control no matter where it is.
No storage location contains all the components necessary to reconstitute the data, making it nearly impossible for information to be exposed or compromised. While at-rest, it's possible for information to not exist in a single geography anywhere in the world, known as jurisdiction independence. This greatly simplifies compliance with data privacy regulations like GDPR, DORA and others.



