There are a growing number of reasons to be concerned when it comes to a company’s data and the data of their customers. Companies have to be cognizant of not just how to backup, secure, protect, and store the data that makes up the life blood of their organization, but also how to be compliant with accessing that data in a safe and secure way.
Calamu’s unique approach to helping protect and manage a company’s data in this complex space is holistic and powerful. But it’s not just the data that a company obtains or produces that is critical (and it is), it is also how that data moves around throughout the company’s employees, systems and infrastructure.
The Calamu Process is designed to be lightweight, fast, secure, and compliant. In order to accomplish this feat, we need to examine a few core concepts of the Calamu Protect™ Platform and how it empowers companies to focus with greater clarity on what makes up that life blood of their organization; their offerings and differentiators.
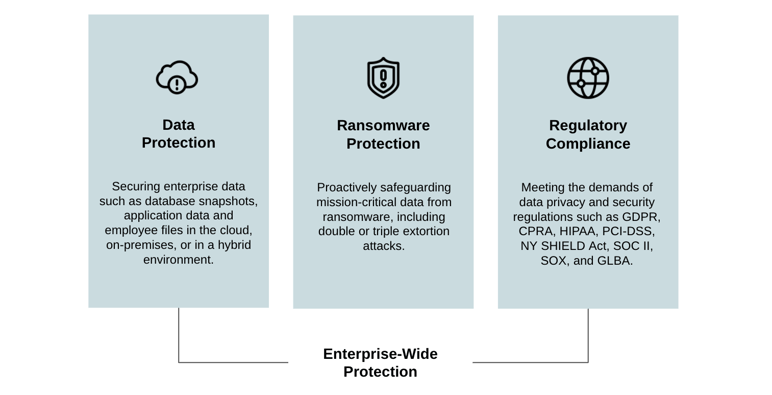
How better to protect data than to make it meaningless to any unauthorized access or bad actor? The core of the Calamu Process is to do just that, as illustrated below:
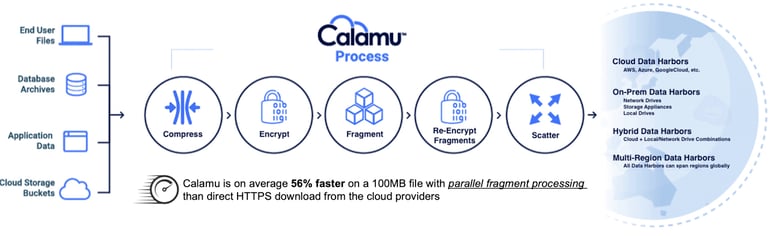
Calamu protects data by identifying data to be protected and ingesting that data as a stream, compressing it if needed, encrypting it, and then breaking up the data (a file for example) into smaller fragments.
Those smaller fragments are re-encrypted using different keys and then scattered to cloud or local storage locations within a data harbor using our proprietary algorithm. The process of scattering the fragments ensures that no single location has all of the fragments required to reconstitute the encrypted data (if each fragment was decrypted against its own key before reassembly). Additionally, the fragments that comprise a file are not all stored in the same cloud provider, nor are they all stored in the same geographic region.
So, the data no longer exists. No single cloud provider and no single geographic region has enough of the fragments to reconstitute the file. The fragments are redundant and securely stored away in the sanctuary of the data harbor.
The data harbor is comprised of a collection of storage locations and includes BYOS, that is, Bring Your Own Storage. This means that each data harbor can be comprised of a company’s privately secured cloud and on-prem storage locations with which to store these meaningless fragments. And there is much more with regards to data harbors.
A number of powerful and unique operations happen within the Calamu Protect™ Platform in order to provide extreme data protection for a company’s data and its piece of mind.
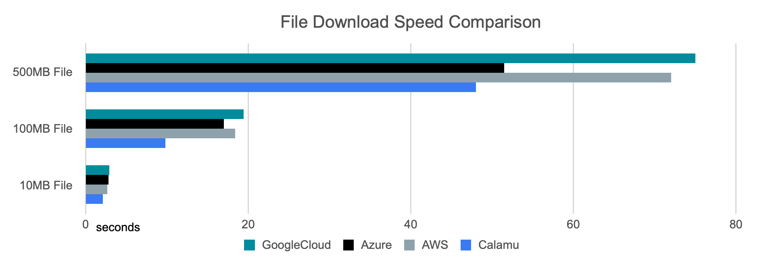
Wouldn’t this slow things down a bit? Not at all. We’ve fine-tuned the performance of the stream-based data protection engine to be exceptionally fast: 56% faster in most cases using a 100MB file size compared to direct cloud upload or download. This is accomplished through parallel fragment processing (horizontal or vertical scale):
Another unique feature of the data harbor is that all of the storage locations within it combine to provide automatic self-healing should an errant process, bad actor, or lifted set of service credentials offer unauthorized access where a fragment is accessed, modified, or removed The location immediately becomes quarantined and the data harbor rebalances to new secure storage locations. No meaningful data can be mined from such an attack as all they store are the double-encrypted and scattered fragments that cannot be reassembled without the Calamu Protect Platform. Double or Tripled Extortion is defeated.
The fragments in the data harbors are immutable within the platform Changes to source data are versioned and fragments cannot be removed outside of the file versioning system itself. This means that lifted credentials are useless for attempts to encrypt and destroy data. Ransomware is defeated.
The Calamu Protect™Platform also includes a uniquely intelligent system of defeating supply-chain attacks and service credentials using expiring down-scoped access tokens.
There is a whole lot more to the Calamu Protect™ Platform that I look forward to writing about. Extreme Data Protection is what Calamu is all about, done without compromising data accessibility. Automatic Data Compliance is a nascent and exciting benefit from this platform as well.
Stay safe, Data.